Dokploy Install - Ditch Vercel, Heroku and Self-Host Your SaaS
Dokploy install and presentation an alternative to serverless like Vercel, Heroku, etc
Dokploy is an open-source, self-hostable Platform as a Service (PaaS) that simplifies the deployment and management of applications and databases using Docker and Traefik. It serves as a free alternative to popular platforms like Vercel, Heroku, and Netlify, offering robust features for developers who prefer to manage their own infrastructure.
If you are interested to see some free cool open source self hosted apps you can check toolhunt.net self hosted section.
Dokploy Features
- Applications: Deploy any type of application (Node.js, PHP, Python, Go, Ruby, etc.) with ease.
- Databases: Create and manage databases with support for MySQL, PostgreSQL, MongoDB, MariaDB, Redis, and more.
- Docker Management: Easily deploy and manage Docker containers.
- Traefik Integration: Automatically integrates with Traefik for routing and load balancing.
- Real-time Monitoring: Monitor CPU, memory, storage, and network usage.
- Database Backups: Automate backups with support for multiple storage destinations.
You can check Dokploy Deploy Apps with Docker Compose if you want to see how you can deploy any application with Docker Compose in Dokploy.
Install Dokploy
New video
Old video
In case you are interested to monitor server resources like CPU, memory, disk space you can check: How To Monitor Server and Docker Resources
Setup A VPS
To get started with Dokploy, you need a Virtual Private Server (VPS). In the video, we go into detail about how you can do that on Hetzner. You can check this Hetzner Review for more details if you are not aware of Hetzner and what it can do.
Hetzner €20 Freessh root@your_vps_ipUpdate System Packages
Before proceeding with the installation, it’s crucial to update your system packages to the latest versions to ensure security and stability:
sudo apt update && sudo apt upgrade -yThis command will update the package lists and upgrade all installed packages to their latest versions.
Create a Sudo User for SSH Access
For security reasons, it’s recommended to use a dedicated user account instead of root for daily operations. Let’s create a user named dragos with sudo privileges:
# Create the new user
adduser dragos
# Add the user to the sudo group
usermod -aG sudo dragosFollow the prompts to set a password and optionally fill in user information.
Configure Passwordless Sudo
To allow the dragos user to execute sudo commands without entering a password (since you’re using SSH key authentication), add the user to the sudoers file:
# Add dragos to sudoers with NOPASSWD
echo "dragos ALL=(ALL) NOPASSWD:ALL" | sudo tee /etc/sudoers.d/dragos
# Set proper permissions on the sudoers file
sudo chmod 0440 /etc/sudoers.d/dragosThis allows you to run sudo commands without password prompts when authenticated via SSH key.
Copy SSH Key from Root to New User
To enable SSH key authentication for the new user, copy the authorized keys from root:
# Create .ssh directory for the new user
mkdir -p /home/dragos/.ssh
# Copy the authorized keys
cp /root/.ssh/authorized_keys /home/dragos/.ssh/
# Set proper ownership and permissions
chown -R dragos:dragos /home/dragos/.ssh
chmod 700 /home/dragos/.ssh
chmod 600 /home/dragos/.ssh/authorized_keysTest SSH Connection with New User
Before disabling root access, verify that you can connect with the new user. Open a new terminal window (keep your current session open) and test:
ssh dragos@your_vps_ipOnce connected, verify sudo access:
sudo whoamiThis should return root, confirming sudo privileges work correctly. Important: Do not close your root session until you’ve confirmed the new user works!
Disable Root SSH Access
Once you’ve confirmed the new user can connect and has sudo privileges, disable root SSH access for enhanced security:
sudo nano /etc/ssh/sshd_configFind and modify the following line:
PermitRootLogin noor
You can allow only certain IP to connect with root in case you need this for the second Dokploy node:
Match User root
PermitRootLogin yes
AllowUsers root@<ip-address>Save the file (Ctrl+X, then Y, then Enter) and restart the SSH service:
sudo systemctl restart sshLimit SSH Session Timeout
To enhance security for idle SSH sessions, especially useful for development environments, set a 15-minute timeout:
sudo nano /etc/ssh/sshd_configAdd or modify these lines:
ClientAliveInterval 900
ClientAliveCountMax 0This will disconnect idle sessions after 15 minutes (900 seconds). Restart SSH to apply:
sudo systemctl restart sshAdd SWAP
Adding swap space can help improve the performance of your VPS by providing additional virtual memory. Follow these steps to add a 2GB swap file:
sudo fallocate -l 2G /swapfile
sudo chmod 600 /swapfile
sudo mkswap /swapfile
sudo swapon /swapfile
echo '/swapfile none swap sw 0 0' | sudo tee -a /etc/fstabSecure Server with CrowdSec
CrowdSec is an open-source security solution that protects your server from brute-force attacks, port scans, and other malicious activities. It’s particularly effective at protecting SSH access.
Install CrowdSec
Add the CrowdSec repository and install the package:
curl -s https://install.crowdsec.net | sudo sh
sudo apt update && sudo apt install crowdsecInstall Firewall Bouncer with iptables
The firewall bouncer uses iptables to automatically block malicious IPs detected by CrowdSec. This will also ensure iptables is installed:
sudo apt install crowdsec-firewall-bouncer-iptables -yAfter installation, verify that CrowdSec has created its iptables chains:
sudo iptables -LYou should see output showing the CROWDSEC_CHAIN has been created and is active:
Chain INPUT (policy ACCEPT)
target prot opt source destination
CROWDSEC_CHAIN all -- anywhere anywhere
Chain CROWDSEC_CHAIN (1 references)
target prot opt source destination
DROP all -- anywhere anywhere match-set crowdsec-blacklists srcConfigure Firewall Rules
Now that CrowdSec is installed and managing its chain, configure iptables to allow only essential services. We’ll allow SSH (22), HTTP (80), HTTPS (443), and Dokploy (3000):
# Allow established connections
sudo iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
# Allow loopback
sudo iptables -A INPUT -i lo -j ACCEPT
# Allow SSH (port 22)
sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT
# Allow HTTP (port 80)
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT
# Allow HTTPS (port 443)
sudo iptables -A INPUT -p tcp --dport 443 -j ACCEPT
# Allow Dokploy (port 3000)
sudo iptables -A INPUT -p tcp --dport 3000 -j ACCEPT
# Drop all other incoming traffic
sudo iptables -P INPUT DROPNote: We use -P INPUT DROP to set the default policy rather than adding a DROP rule at the end. This ensures CrowdSec’s chain remains at the top and processes traffic first.
Make Firewall Rules Persistent
To ensure your firewall rules persist after reboot, install iptables-persistent:
# Install iptables-persistent
sudo apt install iptables-persistent -yDuring installation, you’ll be asked if you want to save current IPv4 and IPv6 rules. Select Yes for both.
After installation, save the current rules:
# Save current rules
sudo netfilter-persistent saveTo update rules in the future, use:
# After making changes to iptables
sudo netfilter-persistent save
sudo netfilter-persistent reloadVerify CrowdSec Installation
Check that CrowdSec is running and monitoring your SSH service:
# Check CrowdSec status
sudo systemctl status crowdsec
# List active collections (should include crowdsecurity/sshd)
sudo cscli collections list
# Verify the firewall bouncer is active
sudo cscli bouncers listThe crowdsecurity/sshd collection is automatically installed and will monitor your SSH logs for suspicious activity.
Test CrowdSec Protection
To verify CrowdSec is actively protecting your server, you can check the iptables rules it manages:
# View CrowdSec managed rules
sudo iptables -L crowdsec-chain -n -v
# View all firewall rules
sudo iptables -L -n -vWhen CrowdSec blocks an IP, it will appear in these chains automatically.
Useful CrowdSec Commands
Monitor CrowdSec activity with these helpful commands:
# View active blocks/bans
sudo cscli decisions list
# Check recent security alerts
sudo cscli alerts list
# View security metrics
sudo cscli metrics
# Monitor logs in real-time
sudo tail -f /var/log/crowdsec.logCrowdSec will now actively protect your server from SSH brute-force attacks and other malicious activities by automatically blocking offending IP addresses.
Install Dokploy
Once your VPS is secured, swap space is added, and CrowdSec is protecting your server, you can install Dokploy using the following command:
curl -sSL https://dokploy.com/install.sh | shThis command will download and run the Dokploy installation script, setting up Dokploy and its dependencies on your server.
Point Your Domain or Subdomain to Dokploy
To access your Dokploy instance via a custom domain or subdomain, you need to configure your DNS settings:
- Log in to your DNS provider: Access the DNS management console of your domain registrar.
- Create an A Record: Point your domain or subdomain to the IP address of your VPS.
For example, to point app.yourdomain.com to your VPS:
Type: A
Name: app
Value: your_vps_ip
TTL: 3600Start Deploying Apps
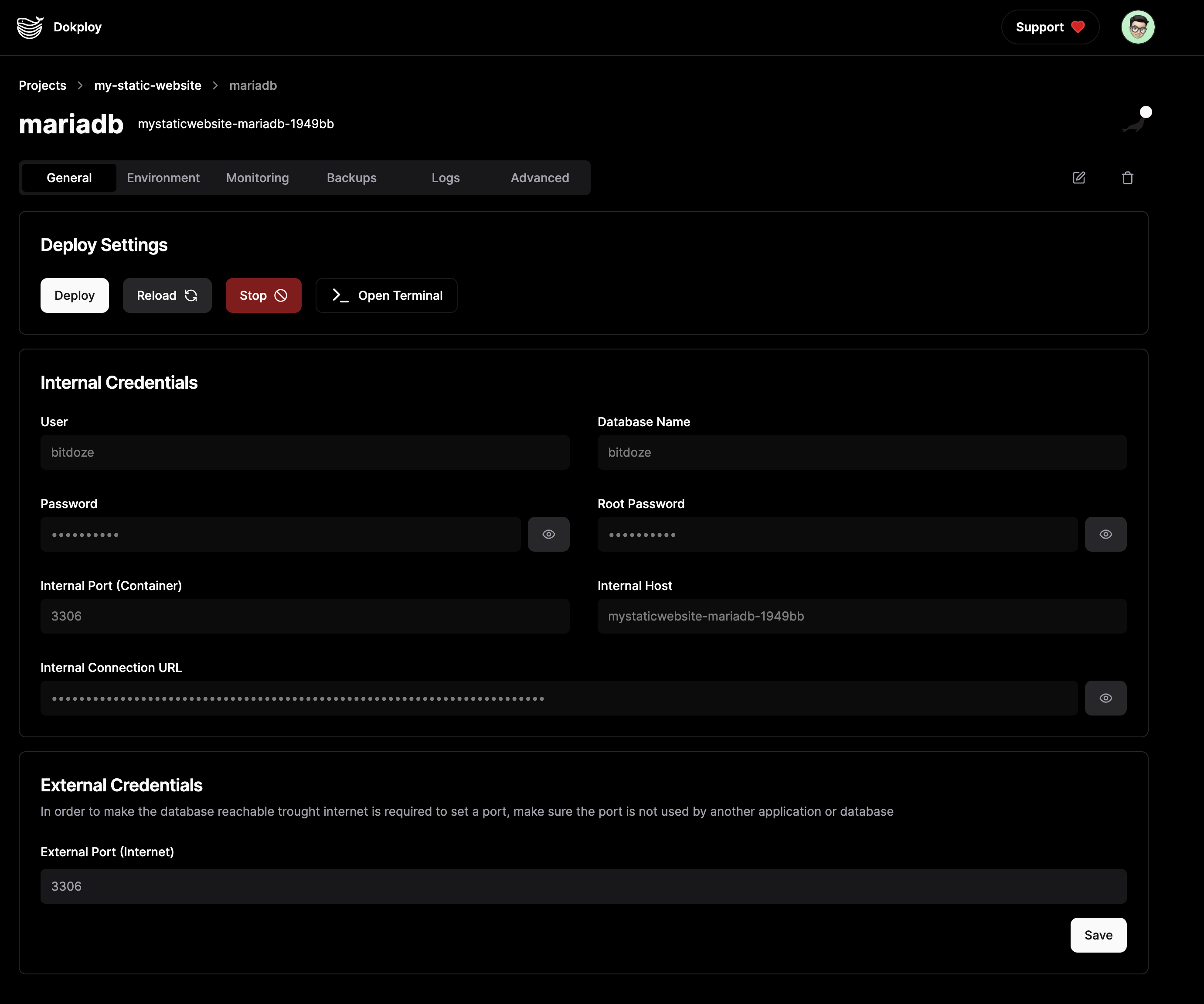
With Dokploy installed and your domain configured, you can start deploying applications. Dokploy supports a wide range of applications and databases, making it easy to manage your projects from a single platform.
- Access Dokploy Dashboard: Open your web browser and navigate to
http://your-ip-from-your-vps:3000. - Create an Admin Account: Follow the on-screen instructions to set up your administrative account.
- Deploy Applications: Use the Dokploy dashboard to deploy and manage your applications and databases.
Conclusions
Dokploy offers a powerful and flexible solution for developers looking to self-host their applications. By following this guide, you’ve not only set up Dokploy but also implemented crucial security measures including:
- System Updates: Keeping your server patched and secure
- User Management: Using a dedicated sudo user instead of root
- SSH Hardening: Disabling root access and implementing session timeouts
- CrowdSec Protection: Actively monitoring and blocking malicious activities
By leveraging Docker and Traefik, Dokploy simplifies the deployment process while providing robust features for application and database management. Combined with proper security practices, you now have a production-ready platform for self-hosting your applications safely and efficiently.


